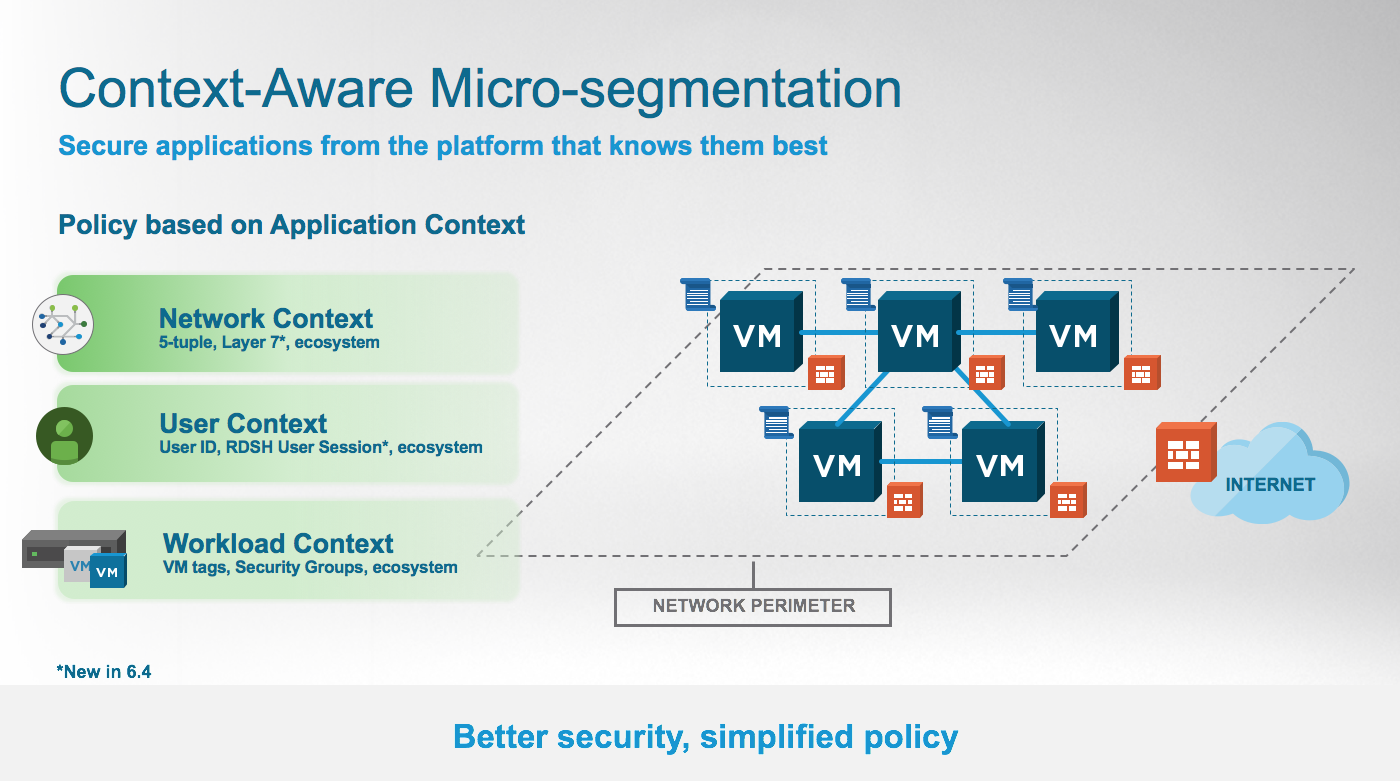
Context- aware firewall enhances the visibility at the application level and helps to override the problem of application permeability. Visibility at the application layer helps you to monitor the workloads better from a resource, compliance, and security point of view.
Firewall rules cannot consume application IDs. Context-aware firewall identifies applications and enforces a micro-segmentation for EAST-WEST traffic, independent of the port that the application uses. Context-aware or application-based firewall rules can be defined by defining Layer 7 service objects.
After defining Layer 7 service objects in rules, you can define rules with specific protocol, ports, and their application definition. Rule definition can be based on more than 5-tuples. You can also use Application Rule Manager to create context-aware firewall rules.
Firewall can take action based on one or a combination of different L2, L3, L4, and L7 packet headers that are added to the data as it moves through each layer of the TCP/IP model.
In layer 3 or layer 4 firewall, the action is taken solely based on source/destination IP, port, and protocol. The activity of network connections is also tracked. This type of firewall is known as a stateful firewall.
Layer 7 firewall is also called as a context-aware firewall. Layer 7 or context-aware firewall can do everything that the layer 3 and layer 4 firewall do. Also, it can intelligently inspect the content of the packets. For example, a layer 7 firewall rule can be written to deny all HTTP requests from a specific IP address.
VMware NSX for vSphere 6.4 Eases Operations, Improves Application Security with Context



