
The Rough Cuts service from VMware Press gives you exclusive access to an evolving manuscript that you can read online or download as a PDF and print. A Rough Cuts book is not fully edited or completely formatted, but you'll get access to new versions as they are created.
Overview
More than 55% of the world's server systems are now virtualized, and 50-60% of today's critical business applications are built with Java. Information about optimizing virtualized systems running Java is critical – and it's remarkably scarce.
Often, there's a mindshare gap” between VMware vSphere administrators and Java developers, who have fundamentally different knowledge and experience. Now, the world's leading expert in Java enterprise virtualization bridges the gap between these fields, offering both the theory and practical solutions that vSphere and Java administrators need to optimize large-scale Java-based systems.
Both a reference and a performance cookbook, Virtualizing and Tuning Large Scale Java Platforms will be indispensable to all technical professionals and IT managers responsible for Java performance in virtualized enterprise systems. Emad Benajmin provides detailed case studies, specific technical advice, troubleshooting help, up-to-date FAQs, and much more. You'll learn how to correctly size, scale, and rationalize virtualized Java platforms; and tune VMware vSphere for the unique challenges of large Java applications.
Benjamin addresses crucial technical issues such as Java garbage collection, and helps you modernize Java application architecture using in-memory databases – preparing your applications for both Big Data and Fast Data. Whether you're virtualizing Websphere, Weblogic, Tomcat, or any other Java-based enterprise application platform, this guide will help you get all the performance, utilization, reliability, and manageability you're paying for.
Start Reading:
Virtualizing and Tuning Large Scale Java Platforms by Emad Benjamin
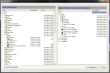 Manfred Meier over at VMwareDirectory has launched a new utility. The vGuestExplorer is a Windows Explorer style tool which can copy files and folders to and from Virtual Machines, even without Network connectivity.
Manfred Meier over at VMwareDirectory has launched a new utility. The vGuestExplorer is a Windows Explorer style tool which can copy files and folders to and from Virtual Machines, even without Network connectivity. 


 The VMware vCloud Automation Solutions lab will accelerate the journey to a lights-out, fully automated, and efficient Software-Defined Datacenter. You can explore vCAC, Orchestrator, PowerCLI and AutoDeploy working together to solve real-world problems.
The VMware vCloud Automation Solutions lab will accelerate the journey to a lights-out, fully automated, and efficient Software-Defined Datacenter. You can explore vCAC, Orchestrator, PowerCLI and AutoDeploy working together to solve real-world problems. A Tech Preview of the exciting new VMware NSX for vSphere product announced at VMworld. Learn how VMware NSX virtualizes your network and simplifies your datacenter. This lab is currently based on a beta version of code and you may encounter some user interface issues during the lab exercises.
A Tech Preview of the exciting new VMware NSX for vSphere product announced at VMworld. Learn how VMware NSX virtualizes your network and simplifies your datacenter. This lab is currently based on a beta version of code and you may encounter some user interface issues during the lab exercises. 


