VMware vSphere 6.5 addresses the operational and security challenges by leveraging the hypervisor to perform the encryption with no modification to the VM. The security architecture of VMware ESXi achieves this goal at the hypervisor layer.
In this document, Mike Foley elaborates on how the security architecture and controls of vSphere VM encryption address the concerns of the security team while providing the IT operations team with the necessary tools to minimize impact on day-to-day operations.
Thursday, January 18. 2018
New White Paper - VMware vSphere 6.5 Virtual Machine Encryption
Wednesday, January 10. 2018
New Technical White Paper - App Volumes Reviewer's Guide
The Reviewer's Guide for VMware App Volumes 2.13.1 is a comprehensive technical overview to help you evaluate VMware App Volumes. App Volumes provides real-time application delivery and life-cycle management. It can use App Volumes to quickly deliver applications and data to users without
compromising the user experience.
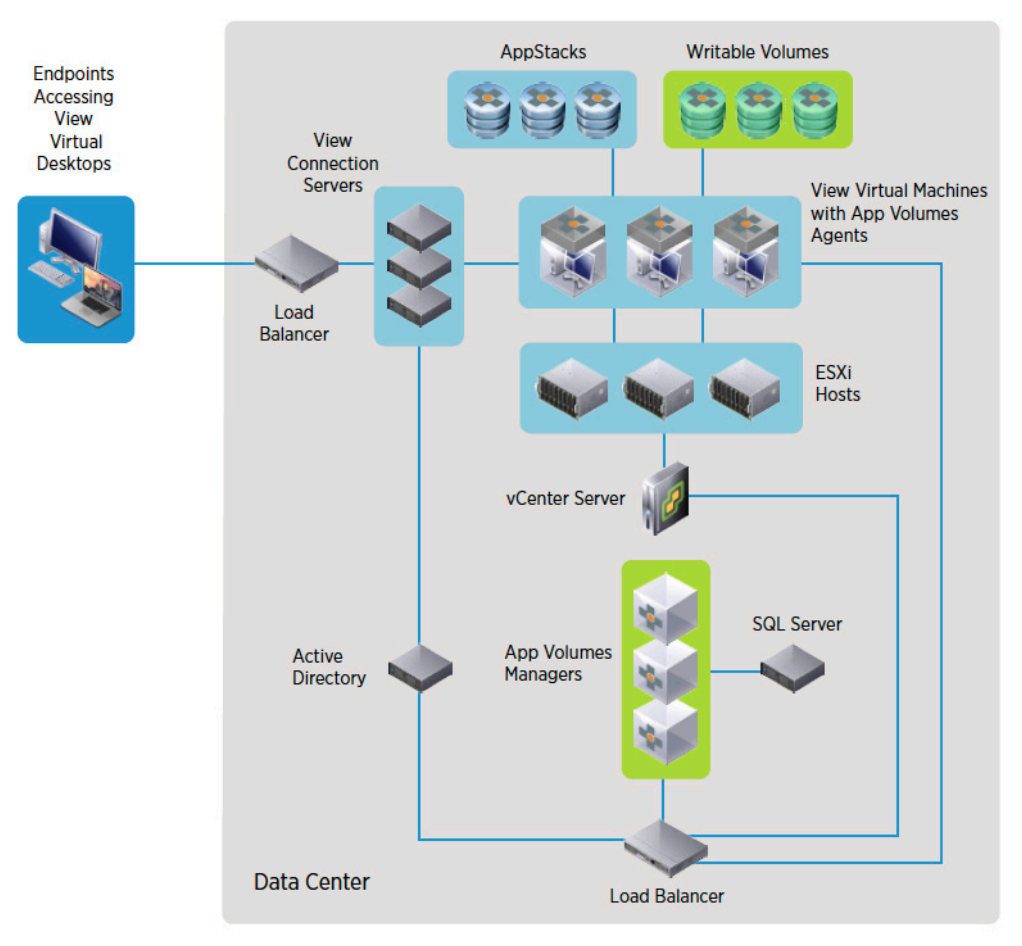
This guide introduces you to App Volumes and how it fits into the VMware End-User-Computing vision. You learn about App Volumes architecture and components, including storage, network, and security. The installation and configuration sections present a basic App Volumes deployment. Exercises in the
remaining sections allow you to evaluate some of the product's key features.
Tuesday, January 9. 2018
Free e-book - Building VMware NSX Powered Clouds and Data Center for small and Medium Businesses
 This book written by Shahzad Ali begins with a discussion around the main VMware NSX for vSphere use cases. Readers are introduced to VMware NSX and its management, control, and data plane components.
This book written by Shahzad Ali begins with a discussion around the main VMware NSX for vSphere use cases. Readers are introduced to VMware NSX and its management, control, and data plane components.
The discussion then moves on to relevant NSX deployment models used in small data centers, offering insight into central aspects of design. After the design and deployment model discussion, the book focuses on implementation aspects of
individual NSX components.
Day 2 operations and troubleshooting topics are extremely important for the success of any deployment. The book examines these concepts, then closes with a discussion on strategies to grow NSX beyond a small data center footprint.
The main objective this book is to provide NSX design and deployment guidance for small and medium businesses (SMBs) with a smaller VMware ESXi footprint.
Regardless of the size of a data center, VMware NSX enables features and use cases that provide business-impacting benefits of agility, reduced CAPEX/OPEX, flexibility, enhanced operations, and monitoring.
This book also discusses design deviations that are permitted for a SMB data center when compared to the reference design and deployment model for large enterprise data centers.
Building NSX Powered Clouds and Data Centers for SMBs is available now
Sunday, January 7. 2018
Free e-learning course - Introduction to Network Virtualization with NSX
 This course also provides an overview of the software-defined data center and explains how NSX integrates with the software-defined data center in the vSphere virtual infrastructure.
This course also provides an overview of the software-defined data center and explains how NSX integrates with the software-defined data center in the vSphere virtual infrastructure.- Explain the role of network virtualization in the software-defined data center
- Explain the fundamentals of physical networking
- Obtain an overview of vSphere networking
- Explain the architecture, features, and use cases of NSX
Friday, December 29. 2017
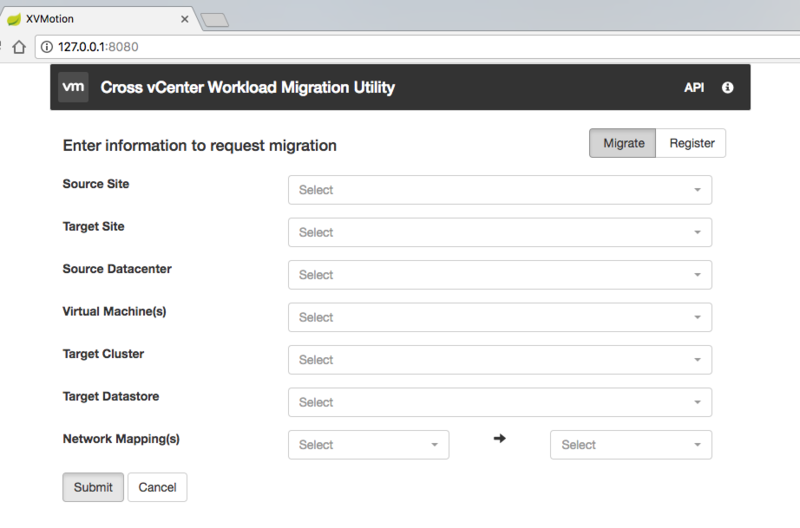
Latest Fling from VMware Labs - Cross vCenter Workload Migration Utility
This Fling allows users to easily migrate virtual machines in bulk from a graphical user interface between vCenter Servers (same & different SSO Domains supported) using the Cross-vCenter vMotion feature.
Key Features
- Completely UI-driven workflow for VM migration
- Provides REST API for managing migration operations
- Works with vCenter not a part of the same SSO domain
- Support for batch migration of multiple VMs in parallel
- Supports both live as well as cold migration of VMs
- Performs storage vMotion, not requiring shared storage
- lexible network mappings between source and destination sites
Also see: Bulk VM Migration using new Cross vCenter Workload Migration vMotion Utility Fling.
Friday, December 22. 2017
ESX IP Storage Troubleshooting Best Practice: Packet Capture and Analysis at 10G
This paper explores the challenges and alternatives for packet capture in a vSphere environment with IP storage (NFS, iSCSI) datastores over a 10G network, and presents the design of a self-assembled 10G packet capture solution that can be built using commercial components relatively inexpensively.
This solution is optimized for common troubleshooting scenarios where short duration packet captures can satisfy most analysis requirements. We recommend vSphere customers deploying ESX IP storage over 10G networks to include 10G packet capture systems as a best practice to ensure network visibility.
Tuesday, December 19. 2017
Free e-book - vSAN Essentials 6.2
 VMware's Virtual SAN has rapidly proven itself in environments ranging from hospitals to oil rigs to e-commerce platforms. Along the way, it has matured to offer unsurpassed features for data integrity, availability, and space efficiency.
VMware's Virtual SAN has rapidly proven itself in environments ranging from hospitals to oil rigs to e-commerce platforms. Along the way, it has matured to offer unsurpassed features for data integrity, availability, and space efficiency.
Virtual SAN 6.x makes all-flash storage practical for even more use cases, while radically simplifying IT operations and supporting the transition to hyper-converged infrastructures (HCI).
Now, the authors of Essential Virtual SAN (VSAN) have thoroughly updated their definitive guide to this transformative technology. Writing for vSphere administrators, architects, and consultants, Cormac Hogan and Duncan Epping explain what Virtual SAN is, how it has evolved, what it now offers, and how to gain maximum value from it.
Saturday, December 16. 2017
New Book - Mastering VMware vSphere 6.5
 VMware vSphere 6.5 written by @Andrea_Mauro @NoLabNoPartY and @novakkkarel provides a powerful, flexible and secure foundation for next-generation applications which helps you create an effective digital transformation. This book will be based on VMware vSphere 6.5 which empowers you to virtualize any complex application with ease.
VMware vSphere 6.5 written by @Andrea_Mauro @NoLabNoPartY and @novakkkarel provides a powerful, flexible and secure foundation for next-generation applications which helps you create an effective digital transformation. This book will be based on VMware vSphere 6.5 which empowers you to virtualize any complex application with ease.
You’ll begin by getting an overview of all the products, solutions and features of the vSphere 6.5 suite, comparing the evolutions with the previous releases. Next ,you’ll design and plan a virtualization infrastructure to drive planning and performance analysis.
Following this , you will be proceeding with workflow and installation of components. New network trends are also covered which will help you in optimally designing the vSphere environment. You will also learn the practices and procedures involved in configuring and managing virtual machines in a vSphere infrastructure.
With vSphere 6.5, you’ll make use of significantly more powerful capabilities for patching, upgrading, and managing the configuration of the virtual environment. Next we’ll focus on specific availability and resiliency solutions in vSphere.
Towards the end of the book you will get information on how to save your configuration, data and workload from your virtual infrastructure. By the end of the book you’ll learn about VMware vSphere 6.5 right from design to deployment and management.
What You Will Learn
- Get a deep understanding of vSphere 6.5 functionalities
- Design and plan a virtualization environment based on vSphere 6.5
- Manage and administer a vSphere 6.5 environment and resources
- Get tips for the VCP6-DCV and VCIX6-DCV exams (along with use of the vSphere 6 documentation)
- Implement different migration techniques to move your workload across different environments.
- Save your configuration, data and workload from your virtual infrastructure.
Friday, December 8. 2017
Video: How to configure encryption in your vSphere 6.5 environment
With vSphere Virtual Machine Encryption, you can create encrypted virtual machines and encrypt existing virtual machines. Because all virtual machine files with sensitive information are encrypted, the virtual machine is protected. Only administrators with encryption privileges can perform encryption and decryption tasks.
An external KMS, the vCenter Server system, and your ESXi hosts are contributing to the vSphere Virtual Machine Encryption solution.
After vCenter Server is connected to the KMS, users with the required privileges can create encrypted virtual machines and disks. Those users can also perform other encryption tasks such as encrypting existing virtual machines and decrypting encrypted virtual machines.
When you create an encrypted virtual machine from the vSphere Web Client, all virtual disks are encrypted. You can later add disks and set their encryption policies. You cannot add an encrypted disk to a virtual machine that is not encrypted, and you cannot encrypt a disk if the virtual machine is not encrypted.
Thursday, December 7. 2017
Free e-learning course - vSphere Integrated Container Fundamentals
This course covers a series of topics on cloud native basics such as container technology, Kubernetes, and container related infrastructure technologies.
- What is a Container? - In this lightboard talk, Ben Corrie explains what a container is for beginners.
- The Benefits of Containers - In this lightboard talk, Ben Corrie walks through the benefits of containers.
- Kubernetes in 5 mins - In this lightboard talk, Steve Tegeler walks through Kubernetes fundamentals for beginners.
- Docker Networking Options - In this lightboard talk, Nathan Ness walks through the networking options in Docker.
- Networking with Kubernetes - In this lightboard talk, Nathan Ness walks through the networking options in Kubernetes and explains the types of communications through Kubernetes services.
- An Analysis of IT Technology Silos: Consumers & Providers - In this lightboard talk, Steve Tegeler takes you through an analysis of IT technology silos and talks about what the consumers and providers of each silo care about.
- Container Registry - In this lightboard talk, Haining Zhang walks you thought what container registry is and how it works.