VMware NSX 4.0.1 delivers a new feature that will enable you to use Stateful Edge services in Active/Active High Availability Mode. Learn more about this new feature in this video.
Tuesday, November 8. 2022
Free e-book - Infrastructure as Code
 This 200+ page ebook is meant to be a step-by-step guide for you to learn how to use some of the most in-demand IaC tools that exist:
This 200+ page ebook is meant to be a step-by-step guide for you to learn how to use some of the most in-demand IaC tools that exist:
- Terraform
- Ansible
- Puppet (and Puppet Bolt)
- Chef
- Salt (aka SaltStack)
Go through the entire ebook to get a sense for what each technology is all about and how it might fit in to what you do. You can always pick a tool and just use that one. Each tool is covered as mostly a stand-alone project that focuses on deploying a simple Docker-based Python web application from Github.
Sunday, November 6. 2022
VMware NSX-T Data Center 3.2 - Easy Adoption Design Guide
 This updated version of the document aligns with NSX version 3.2. It includes the following updates:
This updated version of the document aligns with NSX version 3.2. It includes the following updates:
- NSX vCenter server plug-in for the simple security for applications use case
- Distributed Firewall on vCenter distributed virtual port-groups for VLAN-only micro-segmentation
- NSX Application platform as an optional component to support NSX intelligence and Advanced Threat Prevention features for both the simple security for applications and the data center in a box use cases
- NSX Next-Generation gateway firewall as an optional component for the data center in a box use case
- NSX Advanced Load Balancer as an optional component for the data center in a box use case
VMware NSX-T Data Center 3.2 - Reference Design Guide
 This document provides guidance and best practices for designing environments that leverage the capabilities of VMware NSX®. It is targeted at virtualization and network architects interested in deploying NSX solutions.
This document provides guidance and best practices for designing environments that leverage the capabilities of VMware NSX®. It is targeted at virtualization and network architects interested in deploying NSX solutions.
This updated version of the document aligns with NSX version 3.2. It includes a multitude of updates. Highlights are:
- Updated platform overview and positioning
- OSPF, EVPN, Multicast, Edge HA updates
- Expansion and update of the design guidelines
- Expansion of the performance and optimization guidelines
Friday, October 21. 2022
New Training Course - VMware vSphere: Operate, Scale and Secure [V8]
This five-day course teaches you advanced skills for configuring and maintaining a highly available and scalable virtual infrastructure. Through a mix of lecture and hands-on labs, you configure and optimize the VMware vSphere 8 features that build a foundation for a truly scalable infrastructure. You also discuss when and where these features have the greatest effect. Attend this course to deepen your understanding of vSphere and learn how its advanced features and controls can benefit your organization.
By the end of the course, you should be able to meet the following objectives:
- Configure and manage a VMware Tools Repository
- Configure vSphere Replication and recover replicated VMs
- Manage VM resource usage with resource pools
- Configure and manage vSphere networking and storage for a large and sophisticated enterprise
- Configure vCenter High Availability
- Use host profiles to manage VMware ESXi host compliance
- Use the vSphere Client to manage certificates
- Monitor the vCenter, ESXi, and VMs performance in the vSphere client
- Secure vCenter, ESXi, and VMs in your vSphere environment
- Use VMware vSphere Trust Authority to secure the infrastructure for encrypted VMs
- Use Identity Federation to configure the vCenter to use external identity sources
More information and the schedule can be found here.
New Training Course - VMware NSX: Install, Configure, Manage [V4.0]
This five-day, fast-paced course provides comprehensive training to install, configure, and manage a VMware NSX® environment. This course covers key features and functionality offered in the NSX 4.0.0.1 and NSX 4.0.1 releases, including the overall infrastructure, logical switching, logical routing, networking and security services, firewalls and advanced threat prevention, and more.
By the end of the course, you should be able to meet the following objectives:
- Describe the architecture and main components of NSX
- Explain the features and benefits of NSX
- Deploy the NSX Management cluster and VMware NSX® Edge™ nodes
- Prepare VMware ESXi™ hosts to participate in NSX networking
- Create and configure segments for layer 2 forwarding
- Create and configure Tier-0 and Tier-1 gateways for logical routing
- Use distributed and gateway firewall policies to filter east-west and north-south traffic in NSX
- Configure Advanced Threat Prevention features
- Configure network services on NSX Edge nodes
- Use VMware Identity Manager™ and LDAP to manage users and access
- Explain the use cases, importance, and architecture of Federation
More information and the schedule can be found here.
New Training Course - VMware vSphere: Install, Configure, Manage [V8]
This five-day course features intensive hands-on training that focuses on installing, configuring, and managing VMware vSphere 8, which includes VMware ESXi 8 and VMware vCenter 8. This course prepares you to administer a vSphere infrastructure for an organization of any size.
This course is the foundation for most VMware technologies in the software-defined data center.
Course Objectives
By the end of the course, you should be able to meet the following objectives:
- Install and configure ESXi hosts
- Deploy and configure vCenter
- Use the vSphere Client to create the vCenter inventory and assign roles to vCenter users
- Create virtual networks using vSphere standard switches and distributed switches
- Create and configure datastores using storage technologies supported by vSphere
- Use the vSphere Client to create virtual machines, templates, clones, and snapshots
- Create content libraries for managing templates and deploying virtual machines
- Manage virtual machine resource allocation
- Migrate virtual machines with vSphere vMotion and vSphere Storage vMotion
- Create and configure a vSphere cluster that is enabled with vSphere High Availability (HA) and vSphere Distributed Resource Scheduler
- Manage the life cycle of vSphere to keep vCenter, ESXi hosts, and virtual machines up to date
More information and the schedule can be found here.
Tuesday, October 11. 2022
vSphere 8 What's New? Technical Overview
In this video we will discuss the top new features in vSphere 8, including the brand new vSphere Distributed Services Engine, as well as, enhancements and updates in the areas of vSphere with Tanzu, Lifecycle Management, AI & ML and much much more. For more on everything vSphere 8, check out The Cloud Platform Tech Zone
Saturday, September 24. 2022
To Edge or not to Edge, that’s the question
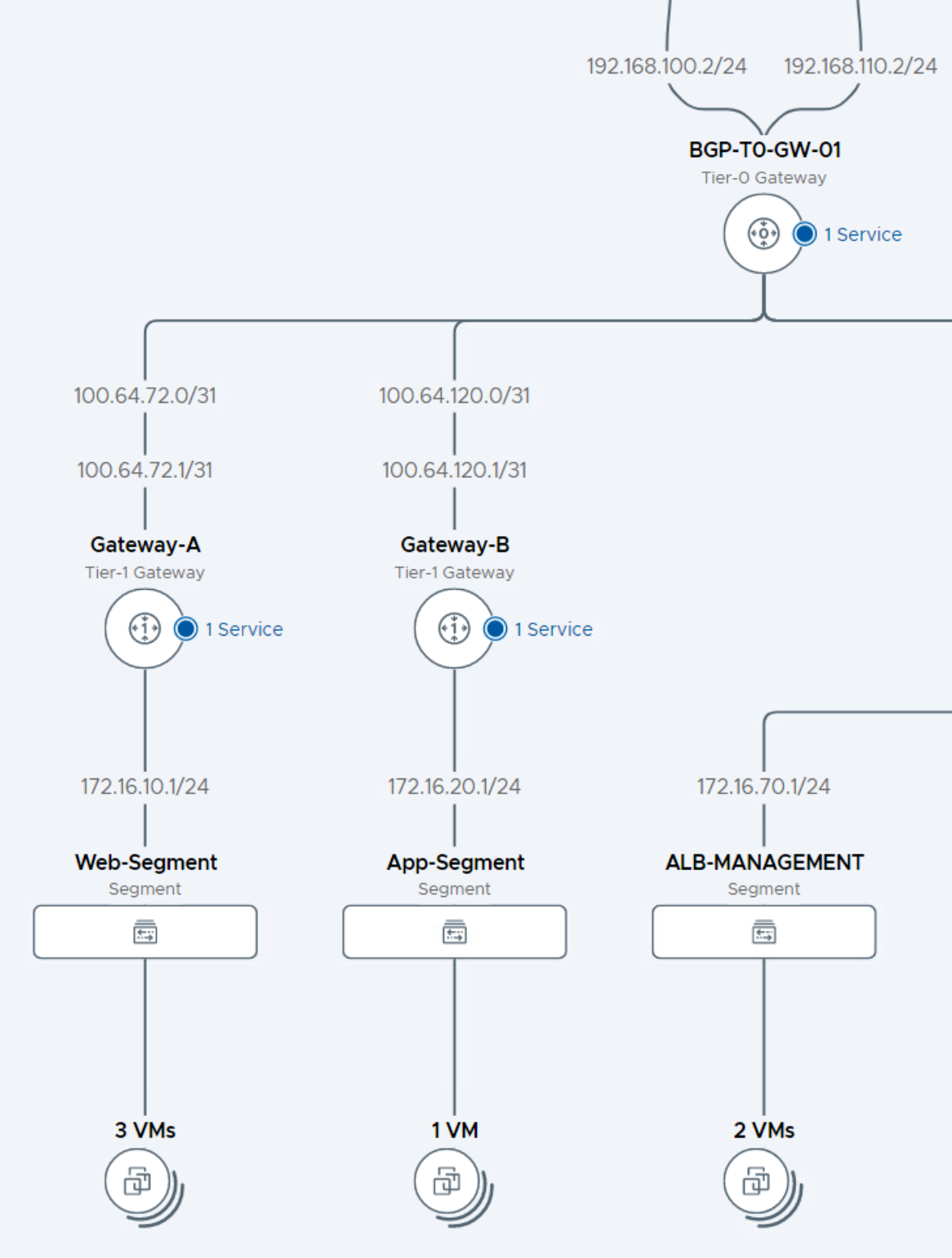
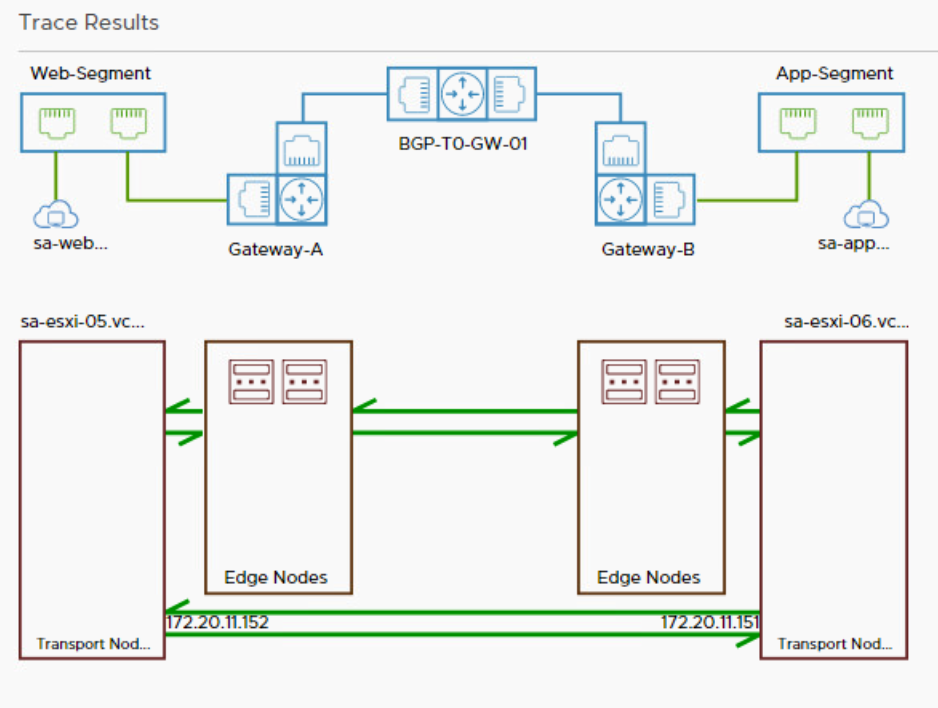
This article describes what the consequences are when configuring an NSX-T Tier 1 Gateway with an Edge Cluster. In my lab environment, I have attached virtual machine sa-web-02 to the Web-Segment, this segment is attached to Gateway-A. The sa-app-01 VM is attached to the App-Segment and this segment is attached to Gateway-B. Both gateways are attached to the BGP-T0-GW-01, a tier 0 gateway.
In the Network Topology overview, there’s also a service active on both gateways. This is the gateway firewall, but since no edges are configured on the Tier 1 gateways. The firewall isn’t active. There is no edge available to host the SRs of these gateway firewalls.
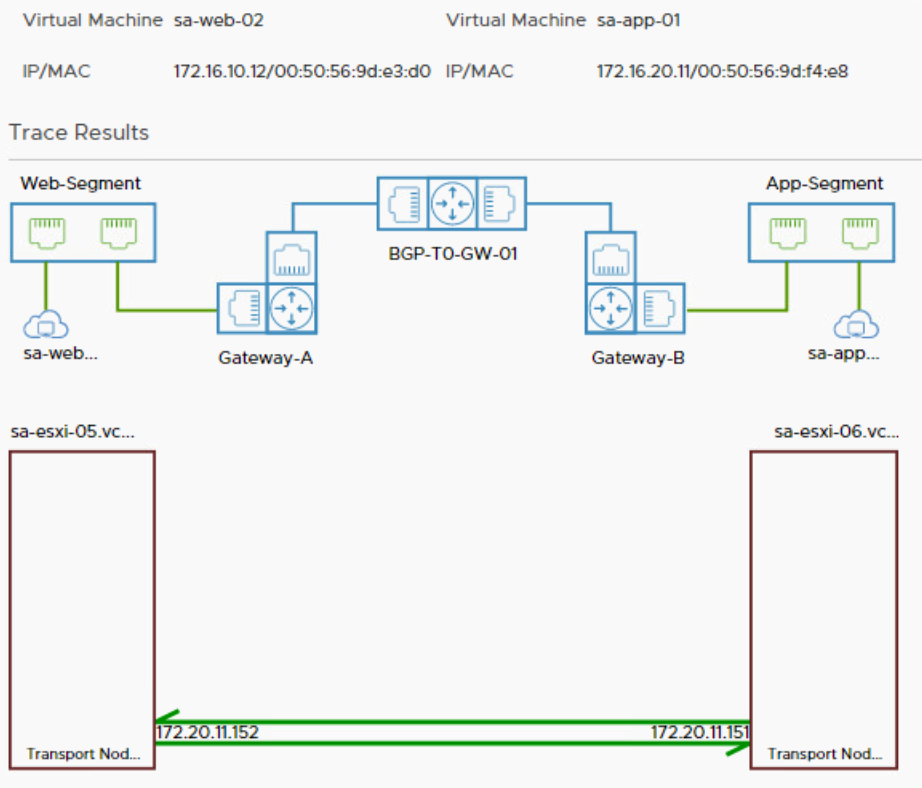
Let’s take a look at the Traceflow troubleshooting tool, available in the Manager user interface.
The packets flow east west through the DR of Gateway-A, the DR of the BGP-T0-GW-01 tier 0 gateway and the DR of Gateway-B. A DR is a distributed router hosted in the kernel of an ESXi host. This all happens on sa-esxi-05 because routing is performed on the host where the packet originates. The source and destination virtual machines are hosted on different transport nodes, that’s why the packets travel through the overlay network between TEPs 172.20.11.152 and 172.20.11.151 after all the routing has been completed.
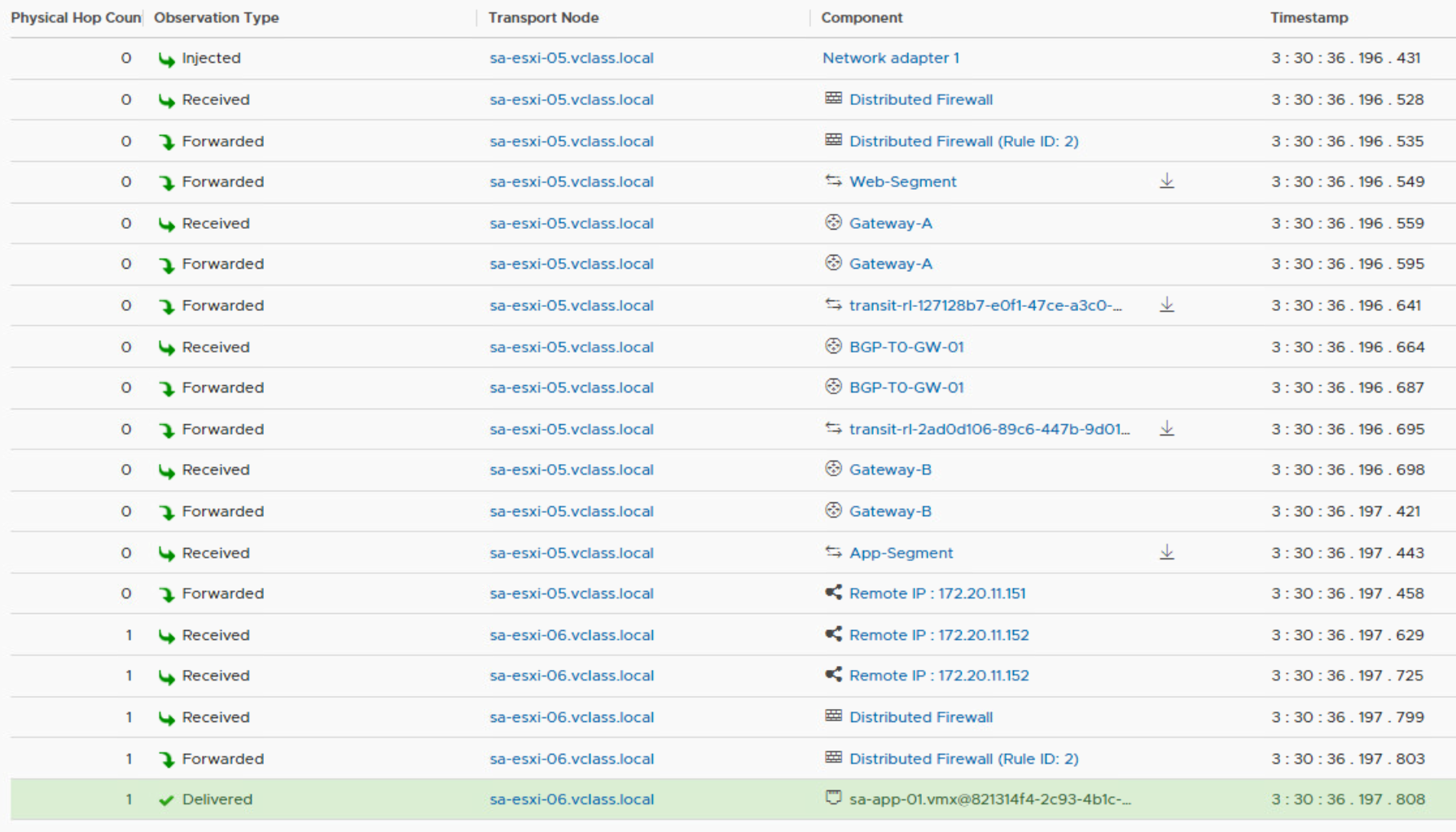
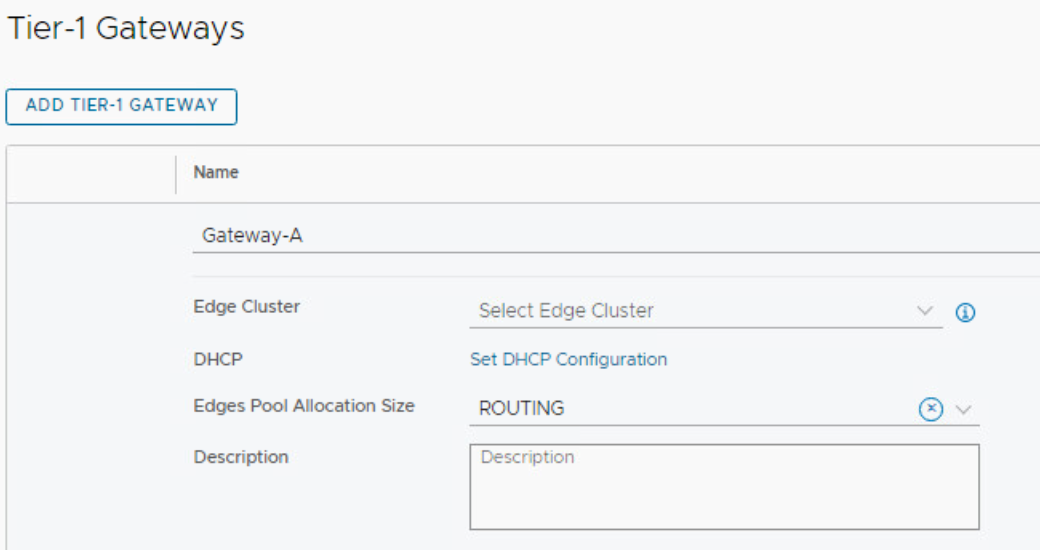
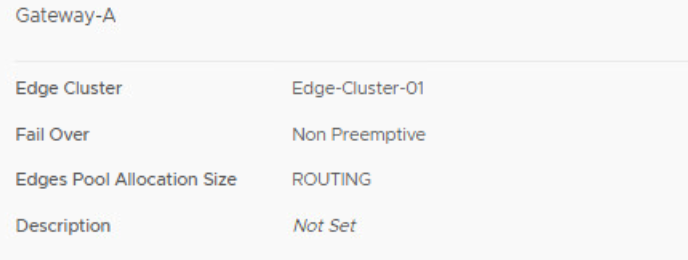
An edge cluster is needed for hosting service routers for the Tier 1 gateways. Services like NAT, gateway firewall, and DHCP are not distributed. When you want to offer these services to a Tier 1 gateway, you need to configure an edge cluster. Let’s configure the gateways with an edge cluster and see what happens.
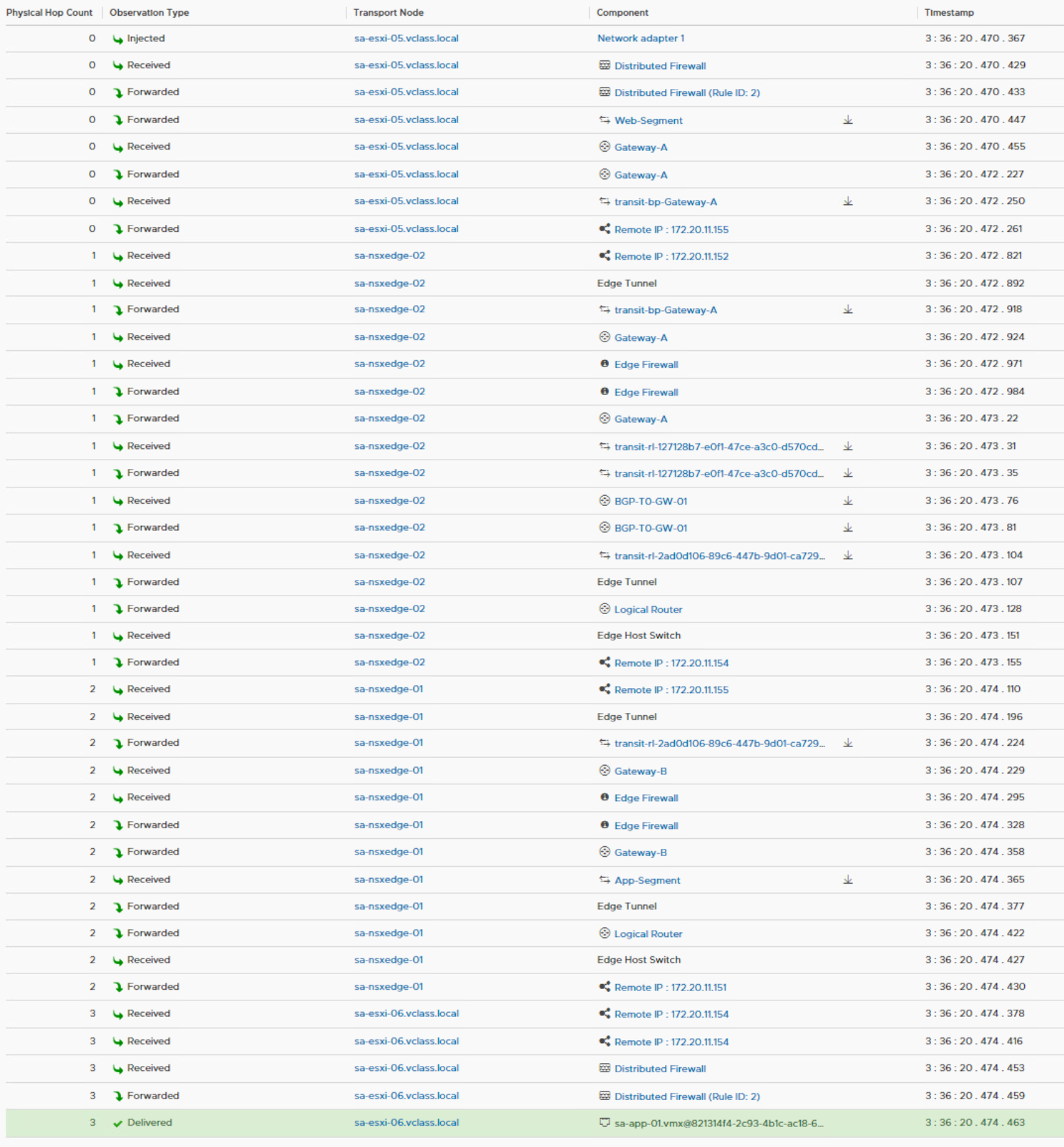
After performing a Re-Trace with the Traceflow utility, we can clearly see that the logical path is the same, but the physical path now contains two edges. This is because both gateways are automatically configured with a north-south firewall. The SR component of these firewalls is hosted on the edges, so the traffic must travel through these edges for the egress and ingress gateway firewall.
Both tier 1 gateways are assigned to a different edge instance in the cluster, so traffic jumps from sa-nsxedge-02 to sa-nsxedge-01. Every time traffic jumps from a transport node to another transport node, the traffic needs to be encapsulated and decapsulated to enter and leave the overlay network. The default firewall rule on a gateway is any-any-allow.
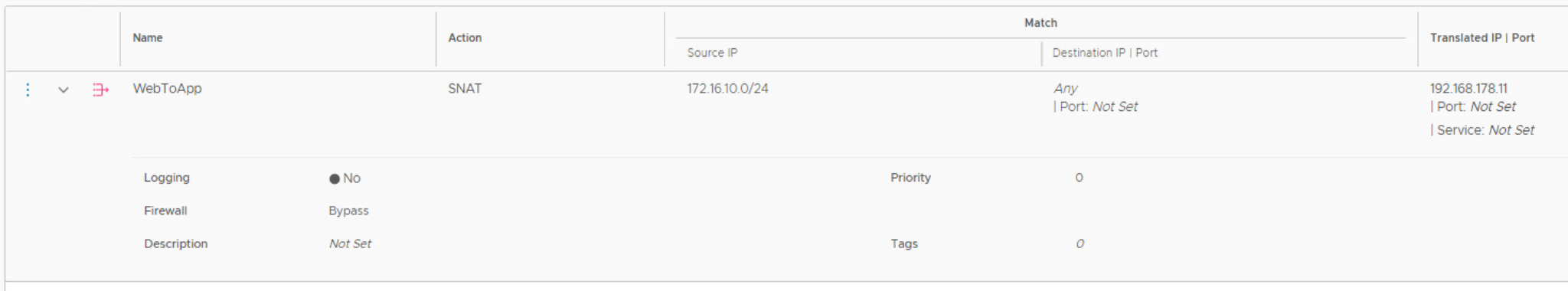
If you want to avoid hair pinning, don’t configure an edge cluster on a Tier 1 gateway. The gateway firewall is always enabled. When you want to offer NAT to segment attached to the Tier 1 gateway, and you must configure an edge cluster, the firewall can be bypassed.
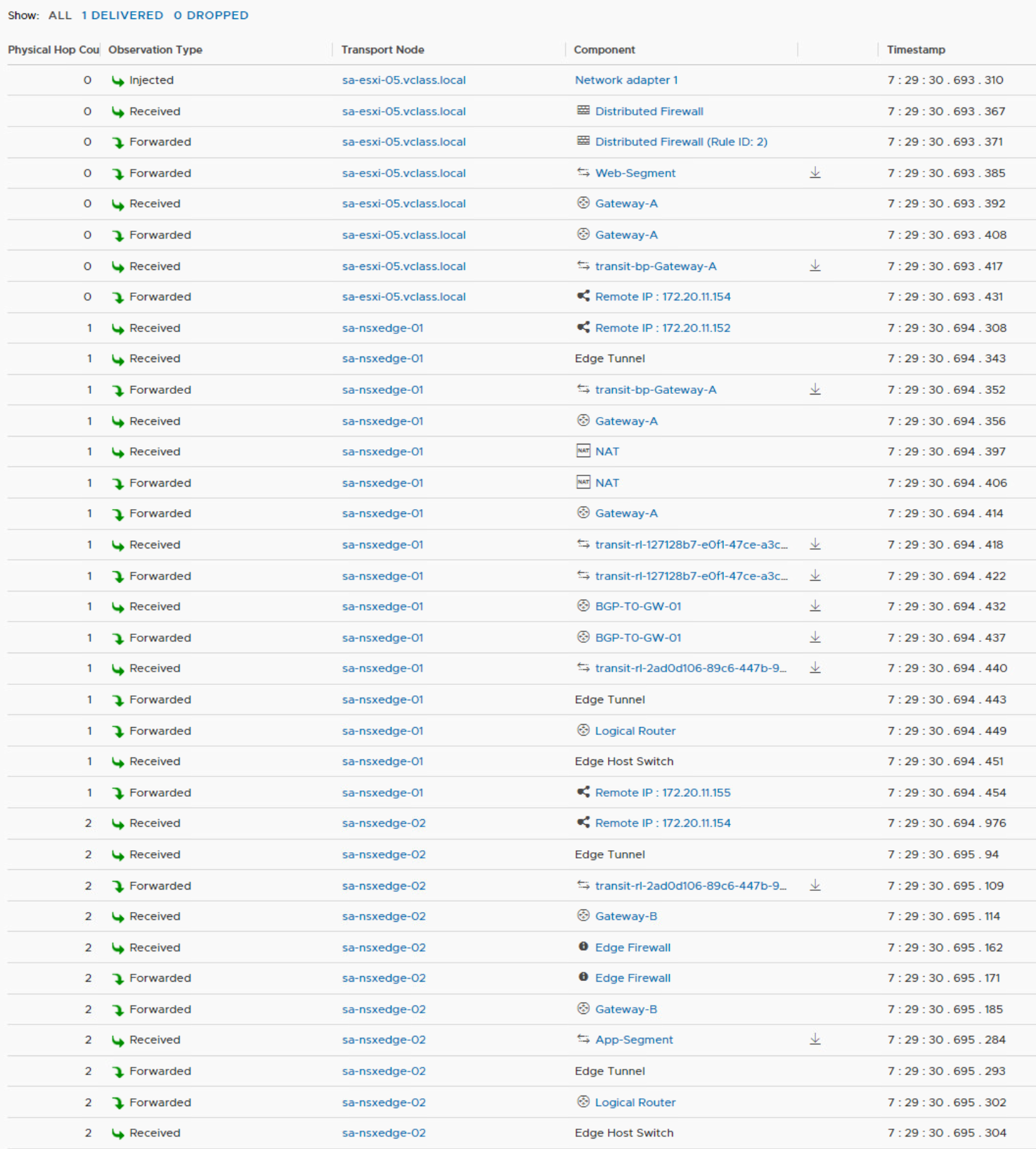
The sequential steps in Traceflow show traffic entering sa-nsx-edge-01 for NAT only, the firewall is not in the data path.
Saturday, September 17. 2022
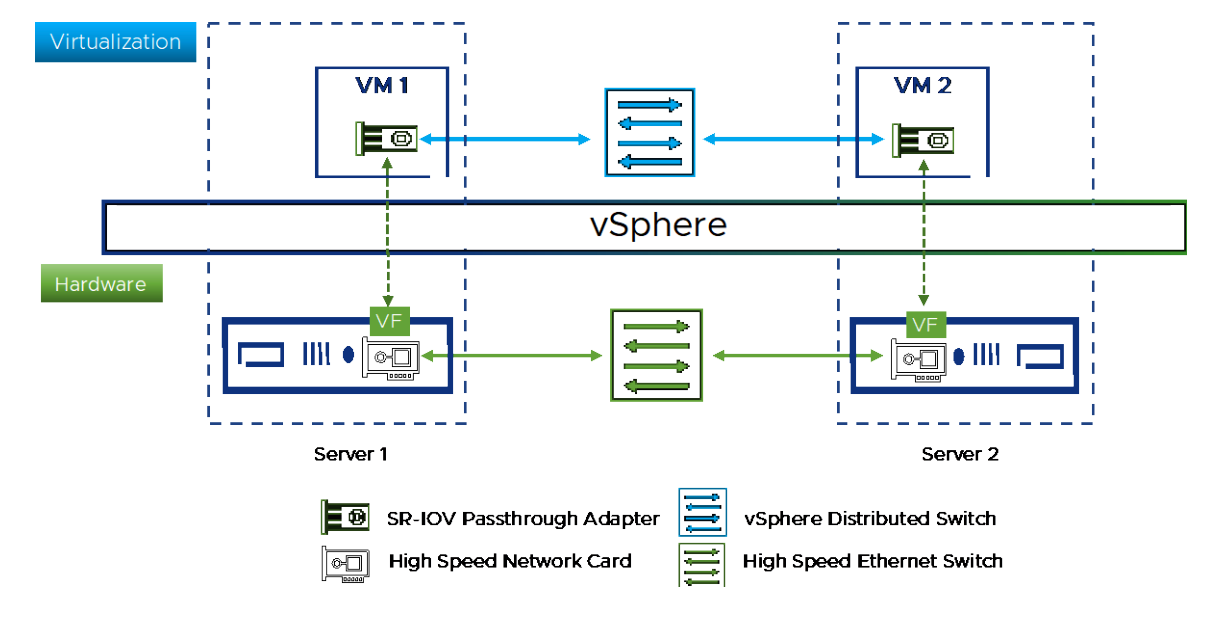
RoCE SR-IOV Setup and Performance Study on vSphere 7.x
In this technical white paper, VMware walks through the steps to enable RoCE SR-IOV on a dual-port Mellanox ConnectX-5 VPI adapter card in VMware vSphere 7.x.
They cover the steps from the BIOS, ESXi, and the vSphere Client to the functionality test on the VM guest operating system. They also introduce how to use the vHPC toolkit, an open-source tool developed by VMware, to speed up the deployment of an HPC cluster in vSphere.
Some of the steps are referenced from VMware documentation on how to configure a VM to use SR-IOV devices and NVIDIA documentation on how to set up and configure the firmware and driver of Mellanox ConnectX adapter cards in a vSphere environment.
Finally, they present a performance study that uses five HPC applications across multiple vertical domains. They conclude that a virtual HPC cluster can perform nearly as well as a bare metal HPC cluster while offering all the advantages of virtualization with vSphere like increased IT agility, flexibility, scalability, and significant cost savings of hardware.